Conceptual diagram of a PDoS attack:
1) Attack sponsor hires botnet herder.
2) Botnet herder uses server to manage recruitment.
3) Malware scans for vulnerable IoT devices and begins cascading infection.
4) Botnet herder uses devices (e.g., HVAC controllers) to deplete bandwidth of a cyber-physical service (e.g., electrical power).
APT: Advanced Persistent Threats (advanced hacking, such as Russia’s APT28 group)
Millions of white label security cameras, DVRs, and NVRs manufactured by Hangzhou Xiongmai Technology Co., Ltd. contain vulnerabilities that can allow a remote attacker to take over devices with little effort, security researchers have revealed today.
Re-branded IP cameras and DVRs sold by over 100 companies can be easily hacked, researchers say.
Millions of security cameras, DVRs, and NVRs contain vulnerabilities that can allow a remote attacker to take over devices with little effort, security researchers have revealed today.
All vulnerable devices have been manufactured by Hangzhou Xiongmai Technology Co., Ltd. (Xiongmai hereinafter), a Chinese company based in the city of Hangzhou.
But end users won’t be able to tell that they’re using a hackable device because the company doesn’t sell any products with its name on them, but ships all equipment as white label products on which other companies put their logo on top.
Security researchers from EU-based SEC Consult say they’ve identified over 100 companies that buy and re-brand Xiongmai devices as their own.
All of these devices are vulnerable to easy hacks, researchers say. The source of all vulnerabilities is a feature found in all devices named the “XMEye P2P Cloud.”
The XMEye P2P Cloud works by creating a tunnel between a customer’s device and an XMEye cloud account. Device owners can access this account via their browser or via a mobile app to view device video feeds in real time.
SEC Consult researchers say that these XMEye cloud accounts have not been sufficiently protected. For starters, an attacker can guess account IDs because they’ve been based on devices’ sequential physical addresses (MACs).
Second, all new XMEye accounts use a default admin username of “admin” with no password.
Third, users aren’t prompted to change this default password during the account setup process.
Fourth, even if the user has changed the XMEye admin account password, there is also a second hidden account with the username and password combo of default/tluafed.
Fifth, access to this account allows an attacker to trigger a firmware update. Researchers say Xiongmai devices firmware updates are not signed, and an attacker can easily impersonate the XMEye cloud and deliver a malicious firmware version that contains malware.
Researchers argue the vulnerabilities they found can be easily used by voyeurs to take over camera feeds and watch victims in their homes. In some cases, some cameras have a two-way audio intercom, so it’s even possible that an attacker may be able to interact with victims as well.
During our research we came across a Xiongmai user manual that contained screenshots with lots of #xmeye cloud IDs. One provided access to a NVR with default credentials at a Xiongmai factory! https://t.co/7NOfZxcqVx pic.twitter.com/n7hsZsUSxy
— SEC Consult (@sec_consult) October 9, 2018
Furthermore, all these devices can be hacked by cyber-espionage groups and be used as entry points inside the networks of targeted organizations, or to relay traffic as part of a technique known as UPnProxy. Cyber-espionage groups, also known as advanced persistent threats (APTs) have been increasingly leveraging routers for their attacks, with the most recent being the VPNFilter botnet, set up by Russia’s APT28 group.
Last but not least, all these Xiongmai devices are also the perfect cannon fodder for IoT botnet herders, who can now mass-scan the XMEye P2P Cloud for accounts with default creds and hijack devices with malicious firmware.
Xiongmai devices have been abused in the past by IoT botnets, and especially by botnets built with the Mirai malware. For example, half of the devices that were part of the massive Mirai-based DDoS attack on managed DNS provider Dyn, which took out around a quarter of the Internet, were Xiongmai devices.
At the time, Xiongmai came under heavy criticism and promised to recall all vulnerable devices.
But SEC Consult claim in a report published today that the Chinese company hasn’t invested in security since patching the vulnerabilities exploited by the Mirai malware in late 2016.
Ever since then, at least four vulnerabilities [1, 2, 3, 4], some at least one year old, were left unpatched, researchers said.
SEC Consult didn’t have much luck when they reported the flaws they found. The company says that despite engaging with both the US and China CERT teams in alerting Xiongmai, the company did not patch the flaws they reported back in March this year.
“The conversation with them over the past months has shown that security is just not a priority to them at all,” SEC Consult researchers said.
Based on scans performed by researchers, there are at least nine million Xiongmai-based devices sitting around on the Internet.
Because none of these devices feature the Xiongmai name or logo, device owners who’d like to take this equipment offline will have a hard time determining if they use one of these vulnerable devices.
SEC Consult says the easiest way to identify a Xiongmai-manufactured (and later rebranded) device is by the equipment’s admin panel login page, which looks like the image below.

In cases where the vendor that bought the Xiongmai devices used a different design for the login page, users can access the device’s error page at http://[device_IP]/err.htm for a second clue. If the error page looks like the image below, then it’s a Xiongmai device.
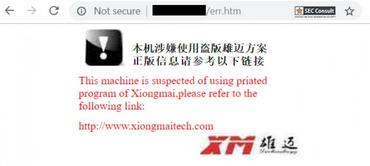
Furthermore, users can find a last clue in their product’s description inside the device’s printed manual, or on Amazon, HomeDepot, or Walmart listings. If the product description mentions anything about “XMEye,” then despite the logo on the front of the device, the equipment was made by Xiongmai.
SEC Consult says it was able to track down more than a hundred other vendors that bought Xiongmai white-label devices and put their logo on top. The list includes names such as:
9Trading, Abowone, AHWVSE, ANRAN, ASECAM, Autoeye, AZISHN, A-ZONE, BESDER/BESDERSEC, BESSKY, Bestmo, BFMore, BOAVISION, BULWARK, CANAVIS, CWH, DAGRO, datocctv, DEFEWAY, digoo, DiySecurityCameraWorld, DONPHIA, ENKLOV, ESAMACT, ESCAM, EVTEVISION, Fayele, FLOUREON , Funi, GADINAN, GARUNK, HAMROL, HAMROLTE, Highfly, Hiseeu, HISVISION, HMQC, IHOMEGUARD, ISSEUSEE, iTooner, JENNOV, Jooan, Jshida, JUESENWDM, JUFENG, JZTEK, KERUI, KKMOON, KONLEN, Kopda, Lenyes, LESHP, LEVCOECAM, LINGSEE, LOOSAFE, MIEBUL, MISECU, Nextrend, OEM, OLOEY, OUERTECH, QNTSQ, SACAM, SANNCE, SANSCO, SecTec, Shell film, Sifvision / sifsecurityvision, smar, SMTSEC, SSICON, SUNBA, Sunivision, Susikum, TECBOX, Techage, Techege, TianAnXun, TMEZON, TVPSii, Unique Vision, unitoptek, USAFEQLO, VOLDRELI, Westmile, Westshine, Wistino, Witrue, WNK Security Technology, WOFEA, WOSHIJIA, WUSONLUSAN, XIAO MA, XinAnX, xloongx, YiiSPO, YUCHENG, YUNSYE, zclever, zilnk, ZJUXIN, zmodo, and ZRHUNTER.
see also: Zmap Scan Project to scan the entire (!)) Internet https://zmap.io/

You must be logged in to post a comment.