White-hat hackers using never-before-seen zero days against popular applications and devices – they competed at a two-day gathering in Chengdu.
Hackers over the weekend successfully compromised widely used software and hardware–including browsers Safari and Chrome, D-Link routers and the Office 365 suite–using zero-day vulnerabilities at the annual Tianfu Cup gathering.
The hacking competition, held in Chengdu, China, is very similar to Pwn2Own, the bi-annual international hacking contest. For two days—Nov. 16 and 17–white-hat hackers compete at the Tianfu Cup to test their skills against popular software and hardware.
However, the contest in China is not an international one. It’s focused solely on Chinese security experts, who used to take part—often with great success–in international competitions until they were prohibited in 2018 by the Chinese government from doing so.
The key aim of the Tianfu Cup is for hackers to take over apps or devices using vulnerabilities that haven’t been seen before.
Competitors—who also compete on the speed with which they can take down systems—can win not only cash prizes, but also earn bragging rights that come with being victorious at a well-respected hacking contest.
Some of the world’s top software and devices proved vulnerable to new zero-day exploits at the event, according to the Twitter feed dedicated to the contest as well as published reports.
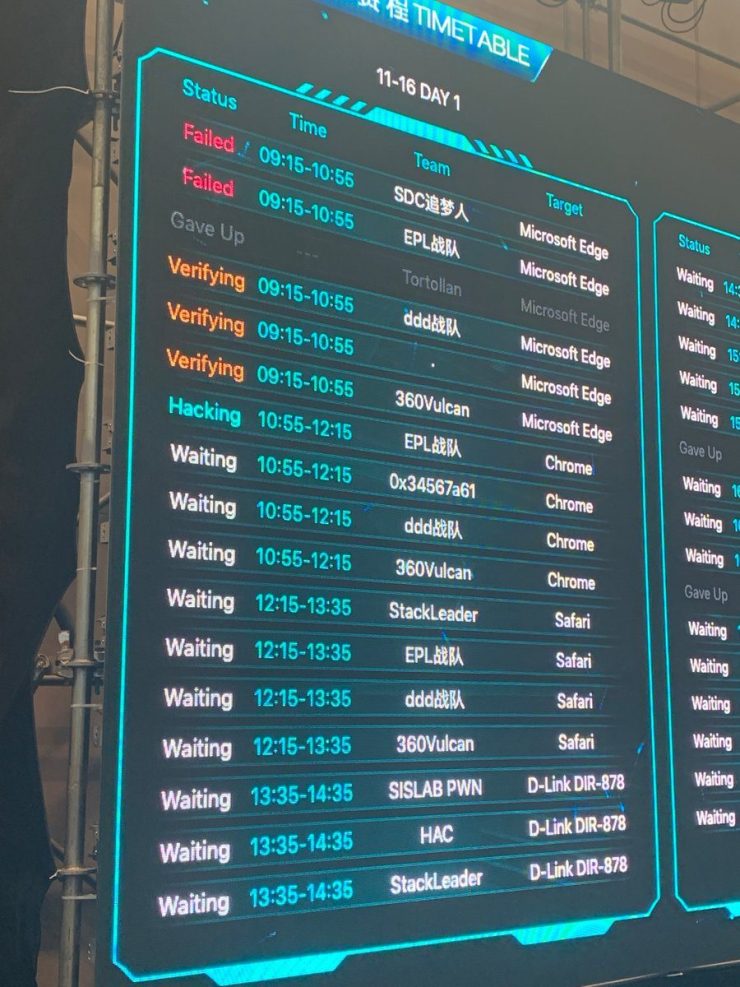
On day one of the competition, teams of hackers successfully used exploits against a number of popular browsers as well as other applications. Organizers said that hackers achieved the following: three hacks against the older version of Microsoft Edge based on EdgeHTML; two hacks against Google Chrome; one hack against Safari; one hack against Microsoft Office 365; and two hacks against Adobe PDF Reader.
Hackers that day also successfully used three exploits to break into and take control of D-Link’s DIR-878 router, as well as compromised qemu-kvm running on Ubuntu.
On day two, four more hacking teams also demonstrated a successful break-in of the D-Link DIR-878 router, while two more teams came out on top again over Adobe PDF Reader, according to organizers.
The big winner of that day, however, was one of the two successful exploits against VMWare that were achieved. Team 360Vulcan hacker @xiaowei won $200,000—the largest bounty of the event—for his hack, organizers said.
Not all the attempts to exploit new zero-day vulnerabilities were successful, however–particularly on day two, organizers acknowledged. Hackers had to give up on eight of 16 hacking attempts that didn’t go as planned that day.
Team 360Vulcan went on to win the event and take home a total of $382,500 for showing off various successful exploits. The team is comprised of well-known hackers who previously won Pwn2Own and are notorious for their skills and persistent activity, one security researcher Tweeted.
“I’m not at all surprised to see 360Vulcan has an exploit in every category,” Twitter user thaddeus e. grugq commented. “They are a large team with a lot of skilled people. Also, they always dominate by quantity in pwn contests, they go after everything.”
***
Pwn2Own Tokyo Roundup:
Amazon Echo, Routers, Smart TVs Fall to Hackers

The latest edition of the bi-annual hacking contest saw creative exploits in new device categories.
Another Pwn2Own has drawn to a close, with Team Fluoroacetate (researchers Amat Cama and Richard Zhu) taking home the Master of Pwn title for the third year in a row.
Overall, contestants in the Tokyo 2019 event earned more than $315,000 over the two-day hacking contest, for uncovering 18 different bugs in the various products. This encompassed new categories for Wi-Fi routers, televisions and smart-home/home automation products, including the pwning of an Amazon Echo. Three teams – Team Fluoroacetate, F-Secure Labs and newcomers Team Flashback – dominated the proceedings.
Most notably, Team Fluoroacetate (which raked in $195,000 overall in the contest) used an integer overflow in JavaScript to compromise Amazon Echo Show 5 and take full control of it (with the device in an RF enclosure to ensure no outside interference). For this, they earned $60,000, the top reward in the event.
“Once patched, this should prove to be an interesting write-up,” according to the Zero-Day Initiative’s blog of the event.
Team Fluoroacetate also took a whack at smart TVs. Their efforts included hacking the Sony X800G smart TV, which was notable for being the first television to make an appearance in the Pwn2Own contest. They were able to use a JavaScript out-of-bounds (OOB) read in the embedded web browser to gain a bind shell (this opens up a communication port to allow an attacker to connect to the device and execute code). They earned $15,000 for that, and also targeted the Samsung Q60 smart TV, earning $20,000 by using an integer overflow in JavaScript to gain a reverse shell from the television.
And finally, the team turned their attention to mobile phones, starting with a knock-out compromise of Samsung’s flagship Galaxy S10 via baseband. They used a rogue base station and a stack overflow to drop a file onto the Galaxy, earning $50,000. Their success marked the third year in a row that Samsung’s flagship handset has been hacked.
They also used a bug in JavaScript JIT followed by a use-after-free flaw to escape the sandbox on the Galaxy S10 via the near-field communications (NFC) component. They were able to steal a picture off the phone with a single tap, reaping a $30,000 reward.
And, in another demonstration, they used a JavaScript bug that jumped the stack to exfiltrate a picture from the Xiaomi Mi9, earning $20,000.

Elsewhere in the competition, F-Secure Labs’ team (Mark Barnes, Toby Drew, Max Van Amerongen and James Loureiro) earned $70,000 overall and came in second place in the Master of Pwn race. Most notably, the team targeted the Xiaomi Mi9 handset via its NFC component, successfully lifting a photo from the phone by tapping it to a rogue near-field communication (NFC) tag. They were able to trigger a cross-site scripted (XSS) bug in the NFC component to send the picture to a different phone that they controlled – earning $30,000.
The team also had partial success pwning the same handset in the web browser category, with two chained logic bugs. One of the bugs was already known to the vendor, but the team still received $20,000 for the effort.
And finally, the F-Secure Labs team targeted the WAN port of the TP-Link AC1750 Smart WiFi router; they combined a command injection bug along with a handful of insecure defaults to be able to execute code on the device, earning $20,000.
Meanwhile, fresh faces Team Flashback (researchers Pedro Ribeiro and Radek Domanski), which wrapped up their first Pwn2Own with a total of $50,000 for four successful demonstrations, also took aim at the TP-Link router with two hacks. They earned $20,000 for a code-execution exploit by targeting the WAN port of the device using a stack overflow combined with a logic bug. And, they used a total of three different bugs – starting with a command injection vulnerability – to compromise the LAN interface of the router and execute code, raking in $5,000.
Team Flashback also targeted the NETGEAR Nighthawk Smart WiFi Router (R6700) with two different demonstrations. They were able to remotely modify the router’s firmware so that their payload persisted across a factory reset – earning $20,000. And, they compromised the LAN interface of the device with a stack-based buffer overflow to gain a shell on the router, earning $5,000 in the process.
Vendors have been notified and have 90 days to produce security patches before public disclosure.
from: https://threatpost.com/pwn2own-tokyo-2019-amazon-echo-hackers/150033/

You must be logged in to post a comment.